What is internet of things “IOT”?
IOT is an ecosystem of connected Smart devices
and it’s sensors that collect and transmit data via internet automatically or
manually according to user choice it’s a called internet of things.
Let’s take
scenarios:-
Okay, Just
think, How many object you had connected with internet about a decades ago 1 or
2 smart devices like (smart phone, smart gadgets etc.) technology. But today
smart desktop, mobile, refrigerator, television ,jockey etc. extends these
trends outward estimated by 2022 there should be around 50 billion objects
connected with the internet. It should be around 6.6 million lives will be
alive so, it is possible that every person has 6 to 7
objects should be connected by internet means world covered with
billions of sensors.
The sensors
are taking information from real physical objects around the world and will
uploaded to the internet. It works with the environment transforms as you walk
through it, because you may not be even not be ware off .It is meandering in
your every move. It’s a world that continuously changing all around us due to
the sensors on the internet .That is called internet of things.
Example: 1
Smart Vehicle automatically will understand the road, signals, and atmospheric
etc. conditions through vehicle sensors.
2. Sensor of
Smart refrigerator, Air-condition, another room equipment will automatically
understand the human’s body temperature from his blood pressure when he entered
in the room and open his refrigerator or any other activity. And many more
examples…
- Internet connected cars
- wearable devices including health and fitness monitoring devices, watches, and even human implanted devices;
- smart meters and smart objects;
- home automation systems and lighting controls;
- smartphones that are increasingly being used to measure the world around them; and
- Wireless sensor networks that measure weather, flood defenses, tides and more.
http://www.technologyguide.com/feature/internet-of-things/
Need of Internet of things
“Imagine a
world in which every device in the home, workplace and car are connected. A
world where the lights automatically turn on when the car approaches the
driveway, the coffee starts brewing when the morning
alarm goes off and the front door automatically unlocks when approached by a
member of the household, but stays locked when a stranger arrives on the front
step. That is the type of world the Internet of Things can create.”
“There are
different companies and organizations that are building out their own platforms
for either their customers or their individual needs.”
“Imagine a
hospital with connected devices. The data collected from those devices outputs
information on the status of patients and runs analytics on the various
monitoring machine, helping the hospital to run as optimally as possible.”
“The
collection of data from devices will allow consumers, businesses and even
entire connected cities to run more efficiently. However, collecting large
amounts of data presents challenges.”
Main challenges, confidentiality,
Integrity, Availability, Non-Repudiations
When you
increase the number of connected devices, the number of opportunities to exploit vulnerabilities through
poorly designed devices can expose user’s data to theft, especially when the
data streams are left with inadequate protection. In certain cases, it may even
harm the safety and health of people.
Confidentiality, Integrity, Availability
and Non-Repudiations
Secondly Privacy
concern for the data that comes with the consumer devices, such as tracking
devices for cars and phones and also smart TVs. Vision features and voice
recognition are now being integrated into smart TVs. These features can listen
continuously to conversations or look for activity and transmit data
selectively to cloud services for processing. These cloud services may
sometimes even include third parties. The collection of all this information
faces a number of regulatory and legal challenges.
Example
Click jacking, Cross-Site Scripting, Path Traversal, Data Validation etc.
Companies
need to ensure they avoid data loss through near-continuous data protection,
verify their protection to guarantee recovery, and use appropriate encryption
to protect against unauthorized access.
In the
modern data center, that often means protecting data at two different physical
sites, as well as protecting the connection between them. And if backups are
stored in the cloud, they need to be under just as much protection.
Finally,
there will be growing emphasis on protecting data while it’s on actual user
devices such as laptops. Endpoint protection is becoming a very important part
of an overall data availability strategy.
Human beings
habituated with smart functionalities with smart gadgets in his day to day
life. Due to this dependencies IOT is non-repudiations.
Why we need to create a structure of
Internet of Things?
The
communication between devices and the Internet or to a gateway includes many
different models:
There are
several reasons why a reference architecture for IoT is necessary:
- IoT devices are inherently connected – we need a way of interacting with them, often/mostly with firewalls, network address translation (NAT) and other obstacles/Problems in the way.
- There are billions of these devices already and the number is growing quickly; we need an architecture for scalability. In addition, these devices are typically interacting 24x7, so we need a highly-available (HA) approach that supports deployment across data centers to allow disaster recovery (DR).
- The devices may not have UIs and certainly/surety are designed to be “everyday” usage, so we need to support automatic and managed updates, as well as being able to remotely manage these devices.
- IoT devices are very commonly used for collecting and analyzing personal data. A model for managing the identity and access control for IoT devices and the data they publish and consume is a key requirement.
Our aim is to provide an
architecture that supports integration between systems and devices.
1. Combination of Three- and Five Layer
of Architectures
It was introduced in the early stages of research in this area. It has three layers, namely, the
perception, network, and application layers.
(i)The perception
layer is the physical layer, which has sensors for sensing and gathering
information about the environment. It senses some physical parameters or
identifies other smart objects in the environment.
(ii)The network
layer is responsible for connecting to other smart things, network
devices, and servers. Its features are also used for transmitting and
processing sensor data.
(iii)The application
layer is responsible for delivering application specific services to the
user. It defines various applications in which the Internet of Things can be
deployed, for example, smart homes, smart cities, and smart health.
The first three layers are not sufficient to research on IOT because technologies are continuous increasing That is why, we have many more layered architectures proposed. The five layers are perception, transport, processing, application, and business layers (Figure 1). The role of the perception and application layers is the same as the architecture with three layers. We outline the function of the remaining three layers.
(i)The transport layer
transfers the sensor data from the perception layer to the processing layer and
vice versa through networks such as wireless, 3G, LAN, Bluetooth, RFID, and
NFC.
(ii)The processing layer is
also known as the middleware layer. It stores, analyzes, and processes huge
amounts of data that comes from the transport layer. It can manage and provide
a diverse set of services to the lower layers. It employs many technologies
such as databases, cloud computing, and big data processing modules.
(iii)The business layer
manages the whole IoT system, including applications, business and profit
models, and users’ privacy. The business layer is out of the scope of this
paper. Hence, we do not discuss it further.
2 Cloud and Fog/Edge Based Architectures:-
In some
system architectures the data processing is done in a large centralized fashion
by cloud computers. Such a cloud centric architecture keeps the cloud at the
center, applications above it, and the network of smart things. Cloud computing
(Online storage, Virtual drive) is given primacy because it provides great flexibility and scalability.
It offers services such as the core infrastructure, platform, software, and
storage. Developers can provide their storage tools, software tools, data
mining, and machine learning tools, and visualization tools through the cloud.
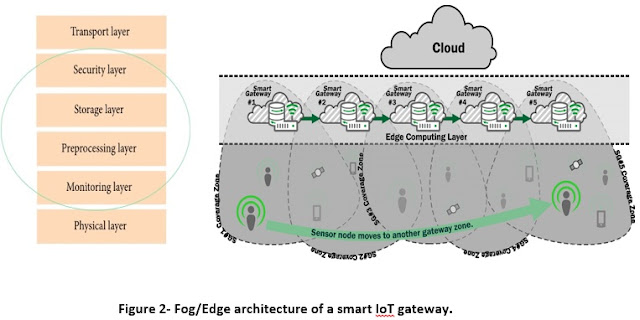
Another system architecture, namely,
fog/Edge computing where the sensors and network gateways do a part of the data
processing and analytics. A fog/Edge architecture presents a layered approach
as shown in Figure 2, which inserts monitoring, preprocessing, storage, and
security layers between the physical and transport layers. The monitoring layer
monitors power, resources, responses, and services. The preprocessing layer
performs filtering, processing, and analytics of sensor data. The temporary
storage layer provides storage functionalities such as data replication,
distribution, and storage. Finally, the security layer performs
encryption/decryption and ensures data integrity and privacy. Monitoring and
preprocessing are done on the edge of the network before sending data to the
cloud.
The term
“fog computing” and “edge computing” term are used interchangeably. Fog
computing originally termed by Cisco refers to smart gateways and smart
sensors, whereas edge computing is slightly more penetrative in nature. This is
an example of imaginations that it is adding smart data preprocessing
capabilities to physical devices such as motors, pumps, or lights. The aim is
to do as much of preprocessing of data as possible in these devices, which are
termed to be at the edge of the network.
Server
side architecture: - The
server connects to all the interconnected components, aggregates the services,
and acts as a single point of service for users. The
server side architecture typically has three layers. The first is the base
layer that contains a database that stores details of all the devices, their
attributes, meta information, and their relationships. The second layer
(Component layer) contains code to interact with the devices, query their
status, and use a subset of them to effect a service. The topmost layer is the
application layer, which provides services to the users.
Device - Device
Architecture: Device
to device communication represents two or more devices that directly connect
and communicate over networks with using Bluetooth, Z-Wave, and ZigBee
protocols.
This
technic is normally used in home automatic systems to transfer small amount of data
packets of information between devices at low data rate. Above is example of
light bulbs, thermostats and door locks sending small amounts of information to
each other.
There
are several standards being developed around Device to device including Bluetooth
low energy. Which is popular among portable and wearable devices because its
low power requirements could mean devices could operate for months or year on
one battery. Its lower complexity can also reduce its size and cost.
Device - Cloud Architecture:
Application service
provider (ASPs): is any company that hosts and manages applications over the
Internet (or WAN) for multiple customers. It includes hosted applications and
also virtual information technology services like virtual servers and operating
systems.
Device-Cloud communication involves an “IoT”
device that will connect directly to an Internet cloud service like an
application service provider (APS) to exchange data and control message
traffic. It uses traditional wired Ethernet or Wi-Fi connections, but can also
use cellular technology.
Let’s take a scenario, a cellular-based Device-to-Cloud would
be a smart tag that tracks your relative while you’re not around, which would
need wide-area cellular communication because you wouldn’t know where the
relative might be.
Another scenario, According to Tschofening, would be remote
monitoring with a object like the Dropcam, where you need the bandwidth
provided by Wi-Fi or Ethernet. But it also makes sense to push data into the
cloud in this scenario because makes sense because it provides access to the
user if they are away. Specifically if you are away and you want to see what’s
on your Dropcam at home. You contact the cloud infrastructure and then the
cloud infrastructure relays to your IOT device.
Device - Gateway Architecture:
Device - Gateway Architecture:
An IoT gateway device bridges the
communication gap between IoT devices, sensors, equipment, systems and the
cloud. By systematically connecting the field and the cloud, IoT gateway
devices offer local processing and storage solutions, as well as the ability to
autonomously control field devices based on data input by sensors.
An IoT gateway performs several
critical functions from translating protocols to encrypting, processing,
managing and filtering data. If you imagine an IoT ecosystem, a gateway sits
between devices and sensors to communicate with the cloud.
Cloud
- Backend Data Sharing:
Back-End Data-Sharing essentially
extends the single device-to-cloud communication model so that IoT devices and
sensor data can be accessed by authorized third parties. Under this model,
users or applications can export and analyze smart object data from a cloud
service in combination with data from other sources, and send it to other
services for aggregation and analysis.
To be continued
Thank you
Nikhil Kumar
IT security Manager and trainer
Cyber Security Studies and research Laboratory (Pune)
cssrl.in